-
Speccy
AskWoody LoungerAugust 24, 2020 at 7:08 pm in reply to: Attempt to start Office 2016 programs fails with error 0xc0000142 #2291039Woody, the 0xc0000142 error code is listed as STATUS_DLL_INIT_FAILED:
{DLL Initialization Failed} Initialization of the dynamic link library %hs failed. The process is terminating abnormally.Office programs attempt to load multiple libraries upon execution and may fail to start during the process if one of those libraries in the memory chain is unable to load.
The “corrupted” library (“restored” by the sfc /scannow command) might be an older version (included in a botched update that incorrectly replaced a newer one) or a library tied to the online licensing verification mechanism (which would explain why an Office365 outage could cause the issue and then suddenly, out of the blue, everything starts to work again with no apparent reason).
Your C:\Windows\Logs\CBS\CBS.log file contents (recorded after the sfc /scannow execution) might shed some light to identify the culprit and, eventually, the reason why that specific .dll file failed to load successfully.
-
This reply was modified 4 years, 8 months ago by
Speccy. Reason: Fixed bold tag
1 user thanked author for this post.
-
This reply was modified 4 years, 8 months ago by
-
Speccy
AskWoody LoungerSame as geekdom here (Win10Pro v1909 x64 Build 18363.959 (Baseline) / 18363.1016 (Beta Testing)),
Antimalware Client Version: 4.18.2007.8 Engine Version: 1.1.17300.4 Antivirus Version: 1.321.1424.0 Antispyware Version: 1.321.1424.0No Windows Defender errors.
That new 4.18.2008.4 platform that Susan and others are talking about is likely a BETA being pushed through whatever preview/fast ring/insider initiatives are currently happening. It may or may not be the next engine to supersede the current one (4.18.2007.8).
IMHO, hacking the Registry (by adding a few REG_DWORD keys) to “flag” the system as a candidate to automatically get a BETA engine to auto-install might not be the smartest move. I would just wait a few more days… When the next engine is “ready” it will be made available through the Catalog, at the usual location:
https://www.catalog.update.microsoft.com/Search.aspx?q=KB4052623Ironically, the supporting KB article at
https://support.microsoft.com/en-us/help/4052623
is also slightly behind: it is still referring the previous engine (4.18.2005.5, made available at the Catalog on June 3rd, 2020).Regarding Redmond’s decision to began flagging some customized HOSTS files as “malicious” one may workaround the “issue” by manually defining an explicit exclusion rule:
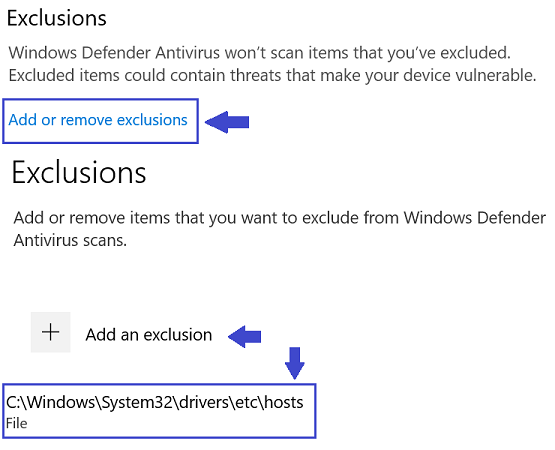
(it may also be viable doing that for multiple endpoints, through a script that ‘reg add”s the rule – although it is a bit tricky as it involves dealing with ownership and permissions, etc)Note however that, because this rule would also allow malware to silently add malicious entries as well, the HOSTS file should always be closely monitored for any unexpected changes.
-
Speccy
AskWoody LoungerWindows Defender Antimalware Client v4.18.2007.8 (1.1.17300.4 engine), v1.321.997.0 definitions, Core isolation OFF, no WD stuff here. Windows Defender Antivirus Network Inspection Service set to Manual, starts fine (normally it is NOT running, it is only triggered and started by the AV itself as needed), no Event Viewer log errors. My 2 cents:
- Core isolation is a device-dependent feature: it can only be enabled successfully if both the hardware and the Hyper-V configuration/usage requirements are met (see here)
- First simple thing to try is to update to the latest definitions (currently v1.321.997.0). They can be manually downloaded at https://www.microsoft.com/en-us/wdsi/defenderupdates (note that the links to download the definitions are often slightly behind the latest available definitions; as I write this, the webpage is still offering v1.321.990.0).
- If problems arise that can be pinpointed solely to the Network Real-Time Inspection component of the product, an alternative to try (instead of reinstalling or rebooting in recovery mode and resetting computers) might be just to scroll down to the bottom of the above mentioned webpage and download and (re)install the NIS updates
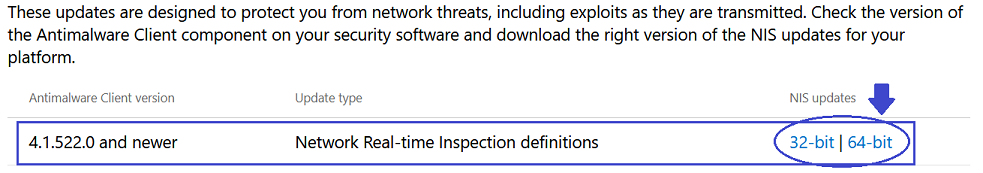
(nis_full.exe is rather old, digitally signed March 21, 2018; I haven’t tried or tested this approach at all, but eventually it might be worth trying – if anyone here wants to confirm that, it might be enough and do the trick of replacing the missing core element – library, whatever – that seems to be the root issue reported by some people) - An even simpler, trustworthy and proved temporary workaround is simply to rollback to the previously used version (v4.18.2006.10-0).
-
Speccy
AskWoody LoungerYes. We’re on Phase 5 now.
-
Speccy
AskWoody LoungerCan’t tell for sure, but it might be a false positive (bitstream scanning of a container format or the content of an object file being incorrectly flagged as a virus).
-
Speccy
AskWoody LoungerDecember 16, 2019 at 3:57 am in reply to: OK Google. Say where is the taxi stand in Portuguese. #2020039Last time I checked, machine translation had a loooong way to go (…)
LOL 🙂 I’ve seen a lot of that, too. Two enlightening and memorable examples of how blindly Google Translate is sometimes used as a lazy way to label consumer products were a permanent ink marker (“marcador de tinta permanente”) being described as “an ink pen with thick and permanent stroke” (badly translated to “caneta de tinta espessa e acidente vascular cerebral permanente”) or a power supply cable being translated to “cabo do poder” (lost in translation)…
Edited for content.
1 user thanked author for this post.
-
Speccy
AskWoody LoungerDecember 15, 2019 at 8:35 pm in reply to: OK Google. Say where is the taxi stand in Portuguese. #2019898The debate goes on whether technology is morally neutral or not but, IMHO, one reasonable middle way might just be that, in the end, albeit morally neutral in the end technology is used in service of people’s values – either in good or bad ways: warrenrumak’s concerns are as pertinent as Noel Carboni’s pragmatism is legitimate.
Back to the topic, Anon is right: Google translates to Brazilian Portuguese rather than European Portuguese (probably because Portugal has a population of 10 million people while Brazil population is over 200 million people).
As EyesOnWindows and OscarCP pointed out, subtle language differences between the two countries and back-and-forth translations often lead to confusing results (to make a comparison, consider the meaning of American English words and expressions such as “sneakers”,”second floor”,”in school” and the British English equivalents: “trainers”,”first floor”,”at school” – see where this is going?).
One small example: shoelaces. The Portuguese (pt-PT) word for it (“atacadores”) is “cardaços” in Brazil (pt-BR). An European Portuguese asking a native Brazilian “Como se apertam os atacadores?” [How do you put your shoelaces on?] will get a weird, slightly afraid look from the Brazilian dude: to him, that question sounds a bit more like “How do you press an attacker?” because the Portuguese expression “um atacante” (an attacker) has the same meaning in both countries (someone who is physically threatening you) but whereas in Portugal, the word “atacador” has one single meaning (a shoelace) in Brazil, it could also be a synonym of “atacante” (an attacker)… thus, unless the Brazilian guy actually faced an angry burglar armed not with a gun but with a pair of big, heavy shoes 🙂 it is pretty obvious how silly the results are!
Not only that, but also Google Translate often does a poor job translating Brazilian Portuguese to English. For e.g. the question “Como apertar os cadarços?” (pt-BR) translates to “How to tighten the shoelaces?” but the same question “como apertar os cadarços?” (pt-BR) all lowercase translates to “how to fasten the shoelaces?” (fasten the shoelaces? really? like, say, fasten your seat belt?)…
There are a few, less-known alternatives to Google Translate – often with better results. DeepL is one such example of a tool providing rather decent results. I left as an exercise to our readers trying to translate the above Portuguese question (“Como se apertam os atacadores?”) into different languages – German, Italian, etc – and then those results back to English… and compare the Google Translate results with the DeepL results.
Edited for content. Please stay on topic. The topic is machine translation of languages, not the merits of the countries of origin.
-
This reply was modified 5 years, 4 months ago by
Bluetrix.
-
This reply was modified 5 years, 4 months ago by
Bluetrix.
-
This reply was modified 5 years, 4 months ago by
Speccy. Reason: Rephrased last sentence
-
This reply was modified 5 years, 4 months ago by
PKCano.
-
This reply was modified 5 years, 4 months ago by
PKCano.
-
This reply was modified 5 years, 4 months ago by
-
Speccy
AskWoody LoungerDecember 7, 2019 at 6:59 am in reply to: MS-DEFCON 4: Time to get the November patches installed #2016006First of all, a quick heads-up: Windows Defender got a new Antimalware Client (Version 4.18.1911.3, engine v1.1.16600.7) yesterday. Quick and Full scans appear to be working fine with current anti-malware definitions (v1.307.20.0 as I write this – more help about this specific subject in my previous post here).
Second, if you haven’t donated yet (guilty! – my bad, sorry…) and have no access to Patch Lady Susan Bradley’s paywalled Patch Watch Column here goes yet another (adding to everyone else’s) additional feedback – reporting back (follow-up of my previous post) from a managed set of Win7/8.1/10 Virtual Machines (VMs) and physical systems: my previously mentioned “Stable BETA TEST” snapshots became the “Stable BASELINE” ones, and the current “Stable BETA TEST” snapshots are now as follows:
Windows 10 x64 (Version 1803):
[Nov 12, 2019] –KB4523203 (2019-11 SSU)
[Nov 12, 2019] –KB4525237 (2019-11 Monthly Rollup) b1130No observable bugs so far, all working fine and normally. System integrity confirmed by executing the SFC /VERIFYONLY and DISM /Online /Cleanup-Image /CheckHealth commands (both successful, no errors returned).
Windows 8.1 x64 (Group A):
[Nov 12, 2019] –KB4524445 (2019-11 SSU)
[Nov 12, 2019] –KB4525243 (2019-11 Monthly Rollup – includes KB4525106 [IE11 Rollup])SSU installed first (manually downloaded from the Catalog), then the Monthly Rollup (WU).
MSRT (Microsoft Malicious Software Removal Tool) v5.77 [Nov 2019] installed successfully via WU, executed normally (no errors).
No observable bugs so far, all working fine and normally. System integrity confirmed by executing the SFC /VERIFYONLY and DISM /Online /Cleanup-Image /CheckHealth commands (both successful, no errors returned).Windows 7 x64 SP1 (Group A):
[Jul 09, 2019] –KB4507004 (.NET Framework 3.5.1, part of KB4507420 [2019-07 .NET Framework Rollup] => Re-released Oct 15, 2019)
[Sep 23, 2019] –KB4474419 (2019-09 SHA-2 v3)
[Nov 12, 2019] –KB4523206 (2019-11 SSU)
[Nov 12, 2019] –KB4525235 (2019-11 Monthly Rollup – includes KB4525106 [IE11 Rollup])
[Nov 12, 2019] –KB4524421 (.NET Framework 4.6.2, part of KB4524741 [2019-11 .NET Framework Rollup])Manually updated using the packages downloaded from Catalog.
No observable bugs so far, all working fine and normally. System integrity confirmed by executing the SFC /VERIFYONLY command successfully (no errors returned).
MSRT (Microsoft Malicious Software Removal Tool) v5.77 [Nov 2019] manually downloaded (before being pulled out from Catalog*) and successfully executed/installed (no errors)*.*Although the Catalog references for applicability of the tool for Windows 7/Server 2008/R2 systems have been pulled out, these were indeed the very same 32-bit/64-bit binaries that remained and are still being offered (currently, for Windows 8.1/10/Server 2012[R2]/2016 only) – more about that here, here, here, here, here and here.
-
Speccy
AskWoody Lounger -
Speccy
AskWoody Lounger -
Speccy
AskWoody LoungerNovember 17, 2019 at 6:27 am in reply to: Born: Microsoft incorrectly signed the MSRT update that’s been bouncing around. It’s fixed now. #2006643“(…) I would say with a high degree of certainty that it is related to the WU agent not understanding the new signing mechanism for this update. It is likely that we will see either a new version of the WU agent released soon, or as an intermediate solution, a new release of the MSRT using the previous signing implementation.”
I agree. It is also my understanding about what might have happened – you nailed it! 😉
(emphasis above, on the possibility of an upcoming, new MSRT to be released soon: it has happened before [December 2008, August 2005] and, in fact, currently the Catalog is not “offering” KB890830 for Windows 7/Server 2008/R2 [that, basically, was the same unique binary currently being offered only for Windows 8.1/10/Server 2012/R2/Server 2016] anymore…)
1 user thanked author for this post.
-
Speccy
AskWoody LoungerNovember 16, 2019 at 5:57 am in reply to: Born: Microsoft incorrectly signed the MSRT update that’s been bouncing around. It’s fixed now. #2006222When manually executed, the KB890830 package will simply unpack MRT.exe to the %WINDIR%\System32 folder and exit the thread, transferring control to it.
Then the %WINDIR%\System32\MRT.exe process will start executing, writing
--------------------------------------------------------------------------------------- Microsoft Windows Malicious Software Removal Tool v5.77, November 2019 (build 5.77.16547.2) Started On Sat Nov 16 11:15:52 2019 Engine: 1.1.16500.1 Signatures: 1.305.993.0 MpGear: 1.1.16330.1 Run Mode: Interactive Graphical Mode
into the %WINDIR%\debug\mrt.log file. Once you press the ‘Next’ button twice, the tool will start scanning (a Quick Scan, by default, if not otherwise selected).
During the scanning process the ‘Version’ REG_SZ registry value remains unaltered: the GUID update in the Registry only happens near the end (when the scanning process finishes – either normally or, presumably, also through an exception catching mechanism if an error occurs and the application ends abnormally):

Then the tool waits for the user input:
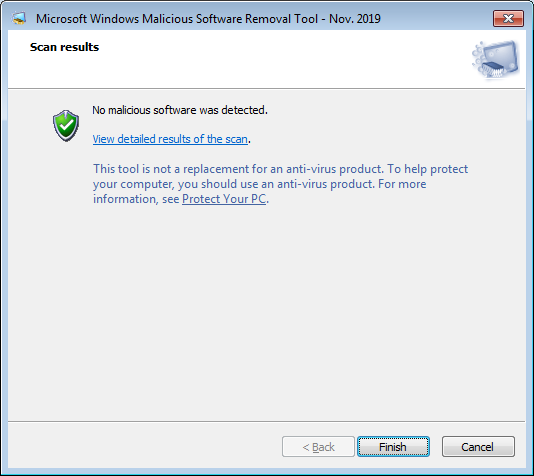
Once the ‘Finish’ button is pressed, the %WINDIR%\debug\mrt.log file is appended with the collected results (and the heartbeat “phone home” attempt occurs – successfully or not, depending if you allow it or not to happen):Results Summary: ---------------- No infection found. Failed to submit clean hearbeat MAPS report: 0x80072EE7 Microsoft Windows Malicious Software Removal Tool Finished On Sat Nov 16 11:28:40 2019 Return code: 0 (0x0)
1 user thanked author for this post.
-
Speccy
AskWoody LoungerNovember 14, 2019 at 5:50 pm in reply to: Born: Microsoft incorrectly signed the MSRT update that’s been bouncing around. It’s fixed now. #2005524A couple more hints on what might have happened (and partially explain why different people are having seemingly random results with WU offering/not offering MSRT upon multiple executions, errors thrown, etc.)…
1) From the KB890830 FAQs:
Q8: Why do not I see the tool on Microsoft Update, Windows Update, or Automatic Updates?
A8: (…) If you have already run the current version of the tool from Windows Update, Microsoft Update, Automatic Updates, or from either of the other two release mechanisms, it will not be reoffered on Windows Update or Automatic Updates.Q9: How do Microsoft Update, Windows Update, and Automatic Updates determine who the tool is offered to?
A9: (…) The users have not already run the current version of the tool.2) From the KB891716 FAQs:
Q2. How do I verify that the removal tool has run on a client computer?
A2. You can examine the [Version REG_SZ] value data for the [HKLM\SOFTWARE\Microsoft\RemovalTools\MRT] registry entry to verify the execution of the tool. (…)
Every time that the tool is run, the tool records a GUID in the registry to indicate that it has been executed:1ED49A70-3903-4C40-B575-93F3DD50B283 (November 2019) E63797FA-851A-4E25-8DA1-D453DD437525 (October 2019)
This occurs regardless of the results of the execution.
3 users thanked author for this post.
-
Speccy
AskWoody LoungerNovember 14, 2019 at 4:39 pm in reply to: Born: Microsoft incorrectly signed the MSRT update that’s been bouncing around. It’s fixed now. #2005472Also, the KB890830 links are currently (as I write this) BROKEN:
- The “Download the x64 MSRT package now.” link should be
https://www.microsoft.com/en-us/download/details.aspx?familyid=585d2bde-367f-495e-94e7-6349f4effc74
(redirecting to https://www.microsoft.com/en-us/download/details.aspx?id=9905)
instead of the broken
http://www.microsoft.com/downloads/en/details.aspx?familyid=585d2bde-367f-495e-94e7-6349f4effc74 - The “Download the x86 MSRT package now.” link should be
https://www.microsoft.com/en-us/download/details.aspx?familyid=ad724ae0-e72d-4f54-9ab3-75b8eb148356
(redirecting to https://www.microsoft.com/en-us/download/details.aspx?id=16)
instead of the broken
http://www.microsoft.com/downloads/details.aspx?familyid=ad724ae0-e72d-4f54-9ab3-75b8eb148356&displaylang=en
Microsoft websites seem to be under major overhauling (with many broken links and contents being moved or deleted).
As an additional tip, some “broken links” might be “fixed” simply by searching for the ENGLISH contents (or manipulating the URL to include ‘/en/’ or ‘/en-us/’). 😉
4 users thanked author for this post.
- The “Download the x64 MSRT package now.” link should be
-
Speccy
AskWoody LoungerUPDATE: Last sentence above should read “(…) for sure, it
willSHOULD execute properly“. As it turns out, my observation is also inaccurate: I had no errors in my preliminary tests – and every clue pointed out to the SHA-2 update being the culprit – but both PKcano and anonymous had different experiences (thank you both for pointing that out).

|
Patch reliability is unclear, but widespread attacks make patching prudent. Go ahead and patch, but watch out for potential problems. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Asking Again here (New User and Fast change only backups)
by
thymej
6 hours, 3 minutes ago -
How much I spent on the Mac mini
by
Will Fastie
51 minutes ago -
How to get rid of Copilot in Microsoft 365
by
Lance Whitney
24 minutes ago -
Spring cleanup — 2025
by
Deanna McElveen
11 hours, 55 minutes ago -
Setting up Windows 11
by
Susan Bradley
1 hour, 26 minutes ago -
VLC Introduces Cutting-Edge AI Subtitling and Translation Capabilities
by
Alex5723
7 hours, 23 minutes ago -
Powershell version?
by
CWBillow
8 hours, 15 minutes ago -
SendTom Toys
by
CWBillow
2 hours, 55 minutes ago -
Add shortcut to taskbar?
by
CWBillow
12 hours, 11 minutes ago -
Sycophancy in GPT-4o: What happened
by
Alex5723
1 day, 4 hours ago -
How can I install Skype on Windows 7?
by
Help
1 day, 3 hours ago -
Logitech MK850 Keyboard issues
by
Rush2112
10 hours, 11 minutes ago -
We live in a simulation
by
Alex5723
1 day, 18 hours ago -
Netplwiz not working
by
RetiredGeek
1 day, 5 hours ago -
Windows 11 24H2 is broadly available
by
Alex5723
2 days, 7 hours ago -
Microsoft is killing Authenticator
by
Alex5723
18 hours, 45 minutes ago -
Downloads folder location
by
CWBillow
2 days, 13 hours ago -
Remove a User from Login screen
by
CWBillow
1 day, 9 hours ago -
TikTok fined €530 million for sending European user data to China
by
Nibbled To Death By Ducks
2 days, 4 hours ago -
Microsoft Speech Recognition Service Error Code 1002
by
stanhutchings
2 days, 4 hours ago -
Is it a bug or is it expected?
by
Susan Bradley
6 hours, 50 minutes ago -
Image for Windows TBwinRE image not enough space on target location
by
bobolink
2 days, 3 hours ago -
Start menu jump lists for some apps might not work as expected on Windows 10
by
Susan Bradley
1 day, 3 hours ago -
Malicious Go Modules disk-wiping malware
by
Alex5723
2 days, 17 hours ago -
Multiple Partitions?
by
CWBillow
2 days, 18 hours ago -
World Passkey Day 2025
by
Alex5723
14 hours, 22 minutes ago -
Add serial device in Windows 11
by
Theodore Dawson
4 days, 2 hours ago -
Windows 11 users reportedly losing data due forced BitLocker encryption
by
Alex5723
2 days, 3 hours ago -
Cached credentials is not a new bug
by
Susan Bradley
4 days, 7 hours ago -
Win11 24H2 Slow!
by
Bob Bible
7 hours, 25 minutes ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.
