-
Windows Insiders: If you’re in the Slow ring, you’re about to get pushed to the next-next version of Win10, version 2003 (a.k.a. 20H1)
Paul Thurrot caught this – it went right over my head.
If you’re one of the (16 million?) folks in the Windows marketing beta… er, Windows Insider program… you should check which ring you’re on. If you’re in the Slow Ring, and are currently beta testing Win10 version 1909, you’ll be switched over to testing Win10 version 2003 (or whatever they’ll call it) “very shortly.”
Paul nails it:
Last night, Microsoft updated a blog post that was originally posted 11 days earlier. This marks the second time they’ve released news to this post by editing the post, and the company seems to be clueless about the fact that these updates are basically sent into a black hole: Without issuing a new post, no one will ever be alerted to the news.
Although I subscribe to the Windows Insider Twitter account, I didn’t notice the tweet. One of my test machines is on the Slow Ring — and it’s about to get pushed to version 20H1/2003. Oh boy.
Anyway, word to the wise, and thanks Paul.
-
Are you still running Win10 version 1803? Microsoft’s pushing hard to get you to 1903
But you don’t have to take it.
If you’re running Win10 Pro (or Education), you can manually move to Win10 version 1809. It’s easy.
Detailed instructions in Computerworld Woody on Windows.
Thx Terry!
-
Seven Semper Fi: Three months to go; here’s what to do.

WOODY’S WINDOWS WATCH
By Woody Leonhard
Time’s running out! Microsoft’s still scheduled to deliver its last Windows 7 security patches on January 14, 2020.
If you plan to continue using your Win7 machines, there’s a variety of tasks you should tackle now to minimize the chances of getting thrown under the bit bus.
Read the full story in AskWoody Plus Newsletter 16.38.0 (2019-10-21).
-
Free tools help prevent Universal Serial Bus slowdowns
LANGALIST
By Fred Langa
Unintentionally mixing devices from USB’s four different generations can be a performance killer.
Trouble is, you can’t always trust the labels and color coding on USB devices; the standards are voluntary, and some manufacturers do things their own way! So it’s not surprising that I’ve received several letters from readers asking for some illumination on this topic.
Here’s how to fully and completely identify every element in your PC’s USB setup — and to see whether your USB devices’ labels and colors really mean what you think they do!
Read the full story in AskWoody Plus Newsletter 16.38.0 (2019-10-21).
-
Microsoft wants to sell you security patches for Win7
WINDOWS 7 SUPPORT
By Amy Babinchak
Given the approaching Windows 7 end of life (January 14, 2020), here’s a surprising development from Microsoft: paid support for all business customers.
Microsoft is, perhaps, bowing to reality — thousands of businesses are not going to migrate to Win10 before the deadline. Whatever the reason, beginning December 1, even small firms will be able to purchase an Extended Security Updates (ESU) license for their Win7 systems.
Read the full story in AskWoody Plus Newsletter 16.38.0 (2019-10-21).
-
The return of our occasional Ultimate Utilities list
ULTIMATE UTILITIES LIST
By T B Capen
Back in my Windows Secrets days, I updated and published the WS Ultimate Utilities List about twice a year. Readers seemed to appreciate it.
Jump forward to 2019, and utilities are just as important as ever — as we highlight in our regular Best Utilities column. Recently, I was reminded of the tools I often use — and some that have gone by the wayside.
Read the full story in AskWoody Plus Newsletter 16.38.0 (2019-10-21).
-
Patch Lady – countdown reminder
Spotted this web site tonight:
https://howmanydaystill.com/its/windows-7-end-of-support-life
86 days and counting
-
Patch Lady – okay Microsoft, how about you help?
So the other day the only place I could find solid actionable information about the risk of attacks from the IE zero day was on a Microsoft 365 ATP E5 console called the Threat analytics dashboard. It was the only place that gave me information that assured me that we could wait until the issues with the patches were dealt with and we didn’t need to rush to patch. Today I went to the console and saw there was a new alert. At the bottom of the alert is brand new wording:
© Microsoft 2019. All rights reserved. Reproduction or distribution of the content of this site, or any part thereof, without written permission of Microsoft is prohibited
Sigh. So there goes another resource that Microsoft is limiting access to just certain paying customers. Once upon a time Microsoft gave actionable information that helped administrators of all sizes to make smarter decisions about security and the risks they face. They told everyone ahead of time on the Thursday before the second Tuesday the types of patches to expect. They had webcasts open to all customers to help all of us understand how to deploy updates better.
Now we have a MSRC blog that just tells us to turn on automatic updates and provides no overall discussion about risks. Thanks guys, but I rushed out that out of band update and spent several HOURS fitzing with printers, updating drivers, removing the update – and in one case had to roll the entire workstation back to the week before to get printing working again. Customers with premier support contracts are the only folks that still get security guidance webcasts. Customers with premier support contracts still get the security patch heads up email on the Thursday before Patch Tuesday.
We’re told by Microsoft that Patching is a social responsibility. Well yes, Microsoft it is. And you have a social responsibility to all of your customers large and small to treat their IT assets with respect. You need to do the right thing and release better patches that don’t break printing (as a recent sample of impact) and you need to release better information to all customers to help us understand the risks of not patching as well as patching. You have a responsibility to all of your customers, and not just those with premier support contracts.
-
Microsoft 365 health status
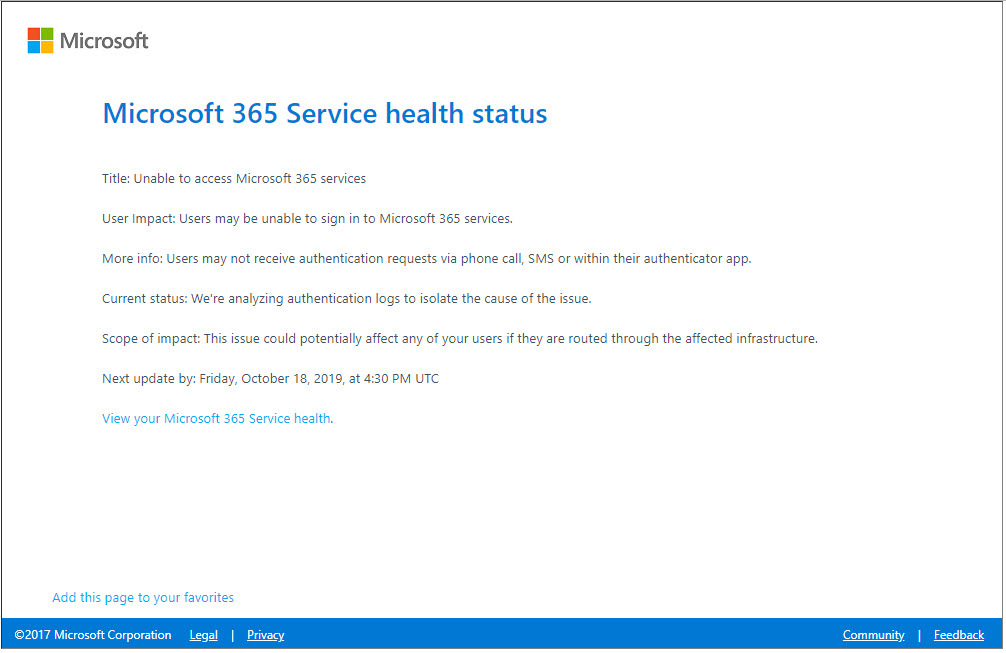
Yes, that’s copyright 2017
Mary Jo Foley has details on ZDNet.
Starting at approximately 13:42 UTC 18 Oct 2019, customers in North America are experiencing issues with Sign-in when Multi-Factor Authentication is enabled. Engineering team is currently investigating the issue and will send out an update as soon as possible.
UPDATE: MS has modified the announcement:
Title: Unable to access Microsoft 365 services with MFA
User impact: Users may be unable to sign in to Microsoft 365 services when leveraging Multi-Factor Authentication (MFA).
More info: Users may not receive authentication requests via phone call, SMS or within their authenticator app.
Current status: We’ve confirmed via telemetry and reports from some of the affected customers that service has recovered for a majority of impacted users. We’re continuing to investigate log data to better understand what caused this issue and to validate which recovery measures we took restored service functionality. Additionally, our telemetry indicates that this issue was specific to users located in the North America region.
Scope of impact: This issue could affect any of your users located in North America if they leverage MFA to access Microsoft 365 services.
Start time: Friday, October 18, 2019, at 1:30 PM UTC Next update by: Friday, October 18, 2019, at 6:30 PM UTC
-
The second “optional non-security” October cumulative update for Win10 version 1809 breaks MS Defender Advanced Threat Protection
Microsoft just acknowledged that KB 4520062, the second October cumulative update for Win10 version 1809 breaks ATP:
Microsoft Defender Advanced Threat Protection might stop running
The Microsoft Defender Advanced Threat Protection (ATP) service might stop running and might fail to send reporting data. You might also receive a 0xc0000409 error in Event Viewer on MsSense.exe.Affected platforms:- Client: Windows 10, version 1809; Windows 10 Enterprise LTSC 2019
- Server: Windows Server, version 1809; Windows Server 2019
Next steps: At this time, we suggest that devices in an affected environment do not install KB4520062. We are working on a resolution and estimate a solution will be available in mid-November.Opened: October 17, 2019 05:14 PM PT
Martin Brinkmann has details on ghacks.net.
Ponder for a moment. This is an “optional non-security” update that breaks a major security feature, used by a large percentage (if not a majority) of Win10 Enterprise customers. Who in blue blazes is testing this stuff?
There’s a reason why we’re on MS-DEFCON 1, eh?
Thx, @Zerafa
-
Announcing the arrival of the Win7 Pro upgrade-to-Win10 nag, KB 4493132
It’s official — and I can confirm. If you install the Win7 patch KB 4524752 on a Win7 Pro machine and reboot a couple of times, you’ll see the new nag screen:

That shot’s taken from my Seven Semper Fi machine, which is now forewarned about impending doom.
OK, I’m being overly dramatic – in fact it all looks like a straightforward nag. As best I can tell, checking “Do not remind me again” actually does take away the nag. But there are some oddities — and a couple of registry settings that send my Spidey sense tingling.
Details in Computerworld Woody on Windows.
-
Liberate the Windows Feedback Hub!
Couldn’t’ve said it better myself….
It sucks that the Windows 10 feedback hub (bug database) is visible only to Windows 10 users who are signed in to feedback hub and whose administrators haven't blocked it.
That's *three* unnecessary restrictions. Just make the bugs visible and searchable on the web! @windowsblog— Bruce Dawson (@BruceDawson0xB) October 16, 2019
The fact that Google (or bing) searches don’t turn up Feedback Hub results is, in and of itself, proof that the Hub is unusable.


