-
Were the January Office security updates just re-released?
Anybody have info on a recent re-release of Office security patches?
On my main production machine (Win10 1703, Office 2013) I just got a Windows Update notification for all sorts of January Office (and Flash) security patches:
- Security Update for Microsoft Office 2013 (KB4011580) 64-Bit Edition
- Security Update for Microsoft Excel 2013 (KB4011639) 64-Bit Edition
- 2018-01 Security Update for Adobe Flash Player for Windows 10 Version 1703 for x64-based Systems (KB4056887)
- Security Update for Microsoft Outlook 2013 (KB4011637) 64-Bit Edition
- Security Update for Microsoft Office 2013 (KB4011636) 64-Bit Edition
- Security Update for Microsoft Word 2013 (KB4011651) 64-Bit Edition
I last installed updates on Feb 5 — when we went to MS-DEFCON 3.
I just re-ran and re-checked the KBNew list. Nothing there from Office 2013.
Did I miss something?
-
Getting out of a no-boot situation after installing Windows updates
@MrBrian has posted a very important addition to the AskWoody Knowledge Base
AKB 2000009: Getting out of a no-boot situation after installing Windows updates
It’s a step-by-step, real world guide to using the Windows Recovery Environment. Might just save your tail one day.
-
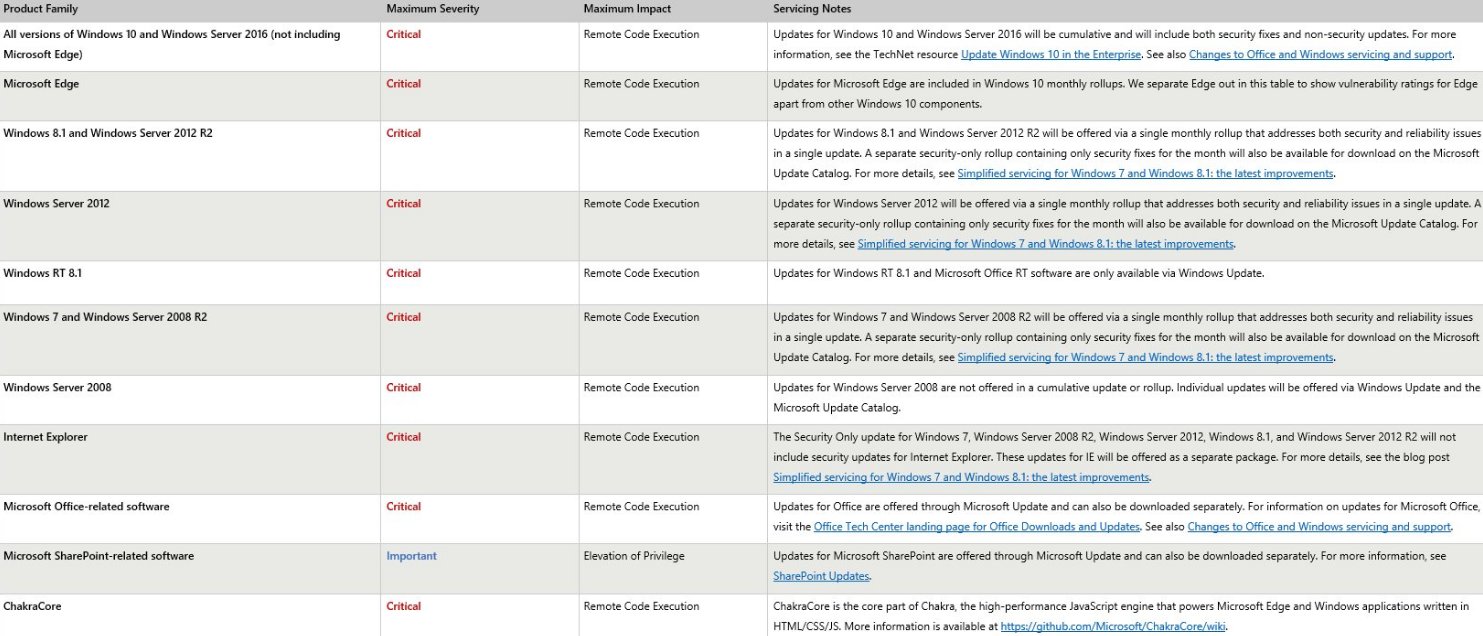
Lots of Critical, Remote Code Execution patches coming on Tuesday
Brian Krebs tweeted an early look at next Tuesday’s patches. Wowza.
-
New version 3.0 of plays-anything-anywhere app VLC
VLC 3.0 launched today.
If you’ve read my books or Computerworld top free apps articles, you know that I strongly recommend VLC. It simply runs rings around anything else.
This new version uses hardware decoding by default, streams to Chromecast (even from video formats that aren’t normally supported), and sports a dozen new features. It’s the first major update in three years.
You might want to wait a few weeks before installing it — just in case. But it’s a dynamite free utility that you’ll want sooner or later.
-
January “security” patches KB 4011657 (Word 2007), KB 4011659 (Word 2010), KB 4011643 (Word 2016), get KB article updates
Thx to @abbodi86 for picking up my earlier mistake.
Here’s another one I found while perusing the KB New list.
It looks like Microsoft just released KB article updates for the January 9 Word security patches, Word 2007, 2010 and 2016.
They’re odd. For example, the Word 2010: January 9, 2018 patch, KB 4011659, lists five CVE numbers — usually an indication that a security problem is being addressed, but the description says:
This security update contains improvements for the following nonsecurity issue:
This update improves Office application startup performance by skipping unnecessary scanning of Microsoft Word documents that are local and not encrypted.
If I read that correctly, this is a “security” update for a “nonsecurity” problem.
Go figger.
I have no idea why the KB articles were re-issued yesterday. Anybody out there have more info?
-
KB 4023057 is back again. Again.
While sifting through the latest KB article change list, I noticed that our old friend KB 4023057 is back.
Now titled Update to Windows 10 Versions 1507, 1511, 1607, and 1703 for update reliability: February 8, 2018, the KB number should ring some bells.
Our own @abbodi86 said this about the last onslaught, in October:
It’s a tool called “Remediation Shell” which remedies “fixes” update-related components to facilitate the upgrade from one version of Win10 to another.
Registry settings, services status, USO and Windows Update SIH (Silent Install Helper), scheduled tasks, disk space, launch Windows10UpgraderApp.exe if installed (included with 1607 cumulative update since June)
I haven’t heard anything new about this latest and greatest version, so I assume that @abbodi86’s description still pertains.
In short, it’s innocuous. Don’t go out of your way to install it, but don’t fear the reaper, either.
UPDATE: Günter Born notes that KB 2952664 for Win7 and KB 2976978 for Win8.1 (both unchecked and optional) were also released yesterday. Born’s take on the Win7 and 8.1 versions is different from mine:
These updates have been good for problems in the past and also had to be withdrawn by Microsoft in some cases. There were machines that hung themselves, where the fan was running at full speed, or where websites or the machine was freezing for short periods of time (see here). Here, here and here are older threads mentions install errors with these updates. Here someone mentions boot issues in November 2017. Weighting all this risks against the benefits of a ‘diagnosis update’, I recommend to hide these updates.
I’m convinced.
-
Intel says its new Spectre-busting Skylake firmware patch is ready
Oh boy. I love the smell of fresh bricked PCs in the morning.
Yesterday, Intel said it has released new firmware that — this time, really, for sure, honest — plugs the Meltdown/Spectre security hole. Says honcho Navin Shenoy:
Earlier this week, we released production microcode updates for several Skylake-based platforms to our OEM customers and industry partners, and we expect to do the same for more platforms in the coming days.
What he’s actually saying is something like, “Hey, we spent six months coming up with new firmware to fix Spectre, released it, and bricked a bunch of machines. We went back to the drawing board and, two weeks later, came up with new firmware that won’t brick your machines. Have at it.”
According to the freshly updated Microcode Revision Guidance, Intel has released updates for Skylake U-, Y-, U23e-, H-, and S- chips.
Shenoy goes on to say:
Ultimately, these updates will be made available in most cases through OEM firmware updates. I can’t emphasize enough how critical it is for everyone to always keep their systems up-to-date. Research tells us there is frequently a substantial lag between when people receive updates and when they actually implement them. In today’s environment, that must change.
To which I say:
Fool me once, shame on me. Fool me twice… well, you know.
Folks, you’d have to be absolutely batbox crazy to install these new BIOS/UEFI patches as they’re being rolled out. Give them time to break other peoples’ machines — or to prove their worth in open combat. I’m sure the folks who made the new firmware are quite competent and tested the living daylights out of everything. But they did that the last time, too.
Again, I repeat, for emphasis, there is exactly NO known Meltdown or Spectre-based malware out in the wild.
-
Adobe Flash patch KB 4074595 pushed out the Windows Update chute
Doncha just love Flash?
A few hours ago, Microsoft pushed the first round of February 2018 patches. The KB 4074595 patch fixes two security holes in Adobe Flash Player, CVE-2018-4877 and CVE-2018-4878.
Microsoft has a few details in Security Advisory ADV180004.
Adobe’s Security Bulletin APSB18-03 says:
Adobe is aware of a report that an exploit for CVE-2018-4878 exists in the wild, and is being used in limited, targeted attacks against Windows users. These attacks leverage Office documents with embedded malicious Flash content distributed via email.
Adobe goes on to say it’s a remote code execution hole. Critical Priority 1. Impacts 28.0.0.137 and earlier versions (February 6, 2018). New version is 28.0.0.161.
Adobe’s version checker is here.
Microsoft’s patches are for Windows 8.1 and Win10, all versions. All of those versions need to have Internet Explorer (and, in the case of Win10, Edge) fixed to plug the holes in the embedded versions of Flash.
Adobe’s patches cover everything other than IE 11 and Edge. Chrome is fixed automatically, by default, when you re-start Chrome.
Liam Tung at ZDNet reports:
Researchers at Cisco Talos said hackers known as Group 123 were using the zero-day Flash flaw and Excel sheets to deliver the ROKRAT remote-administration tool.
Cisco researchers found Group 123’s Excel sheets contained an ActiveX object that was a malicious Flash file that downloaded ROKRAT from a compromised web server. Notably, it was the first time this group has been seen using a zero-day exploit, suggesting the targets were carefully selected and high value.
FireEye, which calls Group 123 TEMP.Reaper, said it had observed the group interacting with their command-and-control infrastructure from North Korean IP addresses. Most of the group’s targets were South Korean government, military and defense industry organizations, it said.
If you haven’t yet disabled Flash, now would be a very good time to do so. Chris Hoffman at How-to-Geek has detailed instructions. If you absolutely have to have Flash, restrict it to one browser — I use Chrome to do the dirty deed — and only use it manually, under duress.
If you can’t or won’t throttle Flash, get the update applied. Yet another Patch Wednesday.
Thx CAR, Günter Born.
-
Even more problems with Surface Pro 4 batteries and Surface TypeCovers
I’ve been covering “flickergate” since last April, and there’s still no resolution from Microsoft — in spite of a recent flare-up in tech blog coverage.
Now, even more complaints are circulating about dead batteries and bricked TypeCovers.
Computerworld Woody on Windows.
-
Outlook 2016 bug “No results when searching All Mailboxes” fixed
Got a note last night from reader KY saying that the old “Search All Mailboxes” bug has been fixed.
Microsoft says that the latest click-to-run version of Office 365 has the fix:
ISSUE
After updating Outlook or Office to version 16.0.8827.2062, searching using the All Mailboxes option shows no results.
STATUS: FIXED
The issue is fixed in Monthly Channel Version 1712 (Build 8827.2179). To get the latest update immediately, open Outlook and choose File > Office Account > Update Options > Update Now.
I wonder if one of the non-security Office 2016 patches this month also provides the fix. (There were three patches specifically for Office 2016 this month.) Darned if I can find any documentation about it, though.
KY confirms that his fix came through Click-to-Run.
-
Microsoft offering free OneDrive for Business to current Dropbox, Box and Google Drive customers
If you have more than 500 users, and you aren’t currently paying for OneDrive, it’s a very inviting offer.
Microsoft says:
We are making it easier for new customers to make the switch by offering free OneDrive for Business for the remaining term of their existing contract with Box, Dropbox, or Google. This offer is valid starting February 6, 2018 through June 30, 2018 for organizations that are not currently OneDrive for Business or Office 365 customers and who make a minimum 500 user commitment.
Microsoft will pay off your existing contract for up to three years.
Of course, MS would like to sell you an Office 365 contract (if you don’t already have one) along with the bargain, but on the face of it, a whole lot of Box, Dropbox and Google Drive customers must be running the numbers.
-
Mind boggling: SpaceX Falcon Heavy
Unbeleeeeeeeevable.
Look here starting about 35 minutes
And a live view of Starman:
To hear about the center booster (which, I fear, may not have landed on its drone ship), follow The Guardian’s coverage.